Customization and Troubleshooting
As you work with Akita, you might want to change what you're seeing or have questions about what Akita is doing. While our goal for is for Akita to be simple and intuitive, we know that all APIs have unique implementations.
This page will cover the most common questions and issues we see.
- I want to hide API endpoints on the Akita web console
- Why is my API model mostly health checks and infrastructure endpoints?
- I'm not seeing the traffic I'm looking for in my API model
- The Akita Agent is not capturing traffic
- What traffic does the Akita agent send to the Akita cloud?
Hide endpoints
If you are seeing endpoints that you don't want to see on the API model and Metrics & Errors page, you can hide them.
Before hiding endpoints, check out our docs on filtering and customizing to make sure those don't solve your problem.
If you would still like to hide endpoints, go to the Diagnostics page to make custom filters to hide traffic you don't want to see.
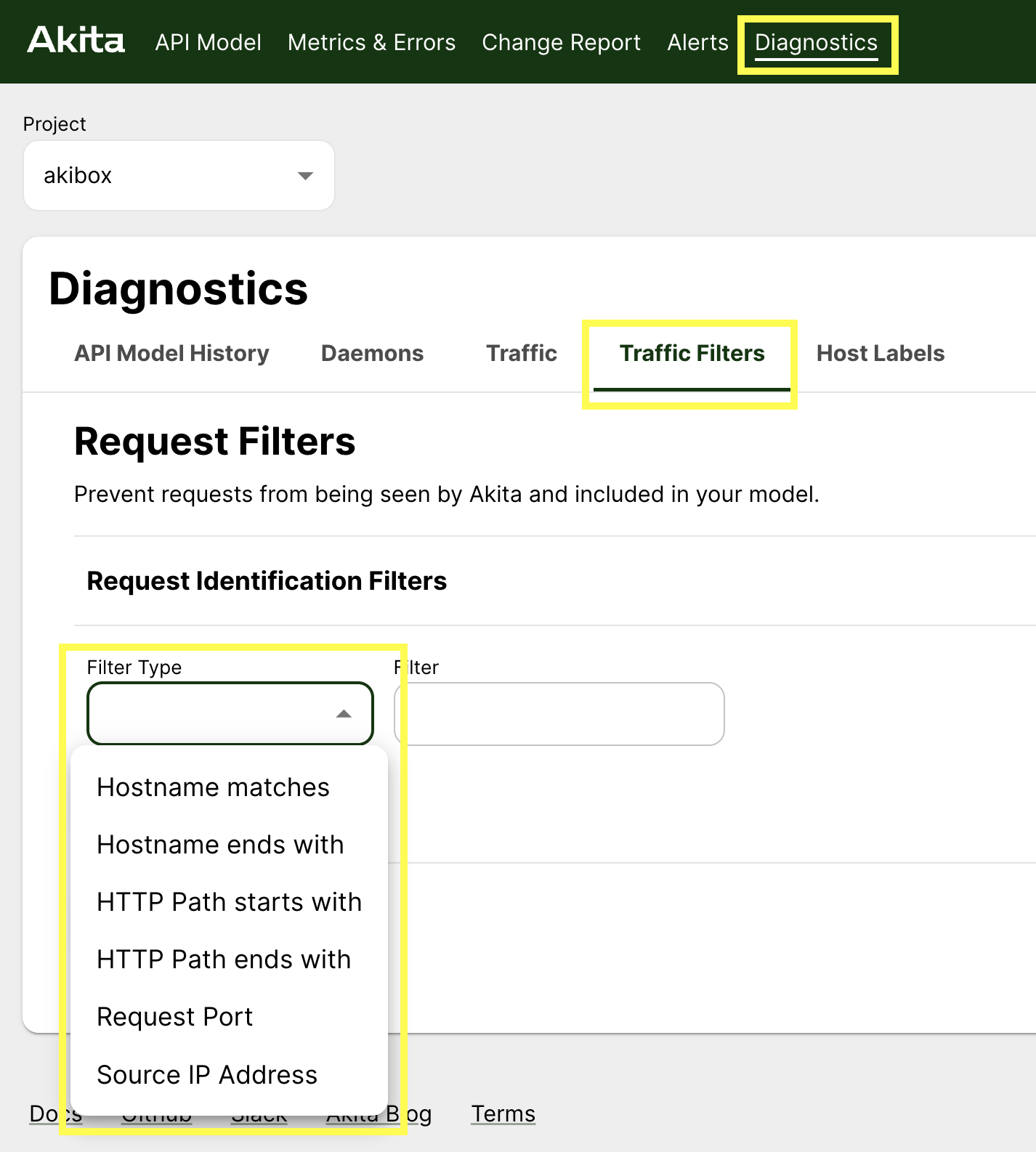
Health checks and Infrastructure endpoints
If you have successfully generates an API model but most of what you're seeing is health checks, that is very normal!
Load balancers and orchestration systems often use a health endpoint to verify whether a service is live. Similarly, there are Kubernetes or AWS endpoints your system may call as part of its regular functioning.
Because these endpoints get called regularly, whether or not there is other traffic, the health endpoints could clog up your API model.
Because Akita samples your traffic, meaning it doesn't send all of your traffic to the Akita Cloud, health check and infrastructure endpoints could come to dominate the traffic that Akita sees. Akita’s rate limiting (which defaults to 1000 calls per minute) may cause some API calls to be dropped— so filtering out the health endpoints ensures that this budget is used entirely for important endpoints.
If this is the case, the solution is to set up filters on the Akita agent. This will increase Akita’s ability to capture meaningful (non-health check) data.
Filtering out endpoints by path
One way to filter out traffic is using the --path-exclusions flag.
To remove a health check endpoint, for instance, use the “--path-exclusions” command line parameter to “apidump”, specifying the path portion of the health check. For example:
apidump –project <your project> –path-exclusions ^/health$
This command will cause all the “/health” endpoints on all hosts to be ignored by the Akita agent.
The argument to –path-exclusions is a Go regular expression, which may match anywhere within the path. The special characters ^ and $ signal “start of string” and “end of string”; this prevents the filter from matching other paths that include the string “/health”, like “/employee/health-benefits”.
Filtering out endpoints by IP address
A similar problem can arise when your model is littered with API calls to unnamed infrastructure services accessed by IP address. To remove these from your model, you can use a regular expression in the “–host-exclusions” command line parameter, as follows:
apidump –project <your project> –host-exclusions ^(\\d)+\.(\\d)+\.(\\d)+\.(\\d)+$
This removes all endpoints whose host is given by a dotted-quad IP address.
Troubleshooting traffic
If you're not seeing the endpoints you're expecting in your first Akita API model, do not worry! There are a few reasons, many of them addressable.
You have different options based on what's going on:
- Few of the endpoints you care about are getting through because they're health checks or infrastructure endpoints. What could be happening is that Akita is seeing mostly health checks and infrastructure endpoints, and your other traffic is not getting through. If that's the case, read above.
- Few of the endpoints you care about are getting through because they're encrypted. If this is the case, see Troubleshooting for workarounds.
- Your model is cluttered with other endpoints that you don't want to see, but that you would like to filter out. If this is the case, try filtering out the endpoints in the Akita console. If the result of that is you end up with very few endpoints in your API models, filter out the endpoints with the Akita agent instead.
Sensitive data
The Akita agent obfuscates request/response payload data and sends only request/response metadata to our servers.
More technically: the Akita agent sends salted hashes of request/response payload data. The Akita cloud is not able to access this information, so the Akita cloud never accesses your sensitive data.
Updated over 2 years ago