Sidecars for Single-Service Kubernetes
How to deploy the Akita Agent in a Kubernetes sidecar.
Getting started with Akita is as simple as dropping our Agent into your service. Below are instructions for installing the Akita Agent as a sidecar for a single service in Kubernetes.
We recommend adding the Akita Agent as a sidecar in your deployment template, the first set of instructions on this page. This should work on any Kubernetes deployment.
An additional option exists if you are using Kubernetes v1.18+ and have Kubernetes alpha features enabled. You can attach the Akita Agent as a sidecar directly to a running container, which will avoid the necessity of making any configuration changes.
Looking to monitor all your services?
When deploying the Akita Agent in a sidecar, it can only monitor other containers in the same pod. You will need to configure a sidecar for each pod you wish to monitor.
As an alternative, we also support deploying the Akita Agent on Kubernetes nodes, which allows Akita to monitor all pods on the node. For more details, see Kubernetes host networking. Note that this will not work if you are using Istio or Envoy, or a reverse proxy in each pod.
Installing the Akita Agent as a sidecar
To get the Akita Agent running in a single Kubernetes service, you will:
- Meet the prerequisites
- Create an Akita Project
- Install the Akita Agent
- Inject and apply the deployment template
- Verify that the Akita Agent is working
When you’ve completed the steps, you can also look at what is needed to scale your Akita deployment.
Thanks to Bruno Felix, who experimented with this method and provided us with his examples!
Prerequisites
Akita Account Required
You must have an Akita account to use Akita. You can create an account here.
Your Kubernetes service must:
- have access to the public internet
- use unencrypted HTTP
- be able to be restarted, as the installation process will cause a restart
Create a project
Log into the Akita App, and go to the Settings page.
Enter a project name and click "Create Project". We suggest naming the project after your app or deployment stack.
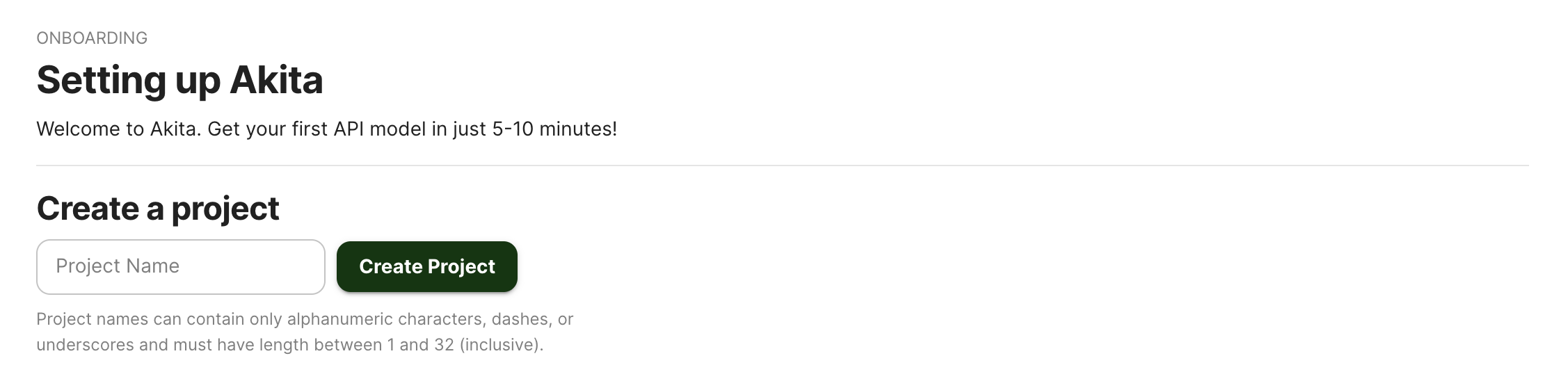
Give your project a name that's easy to remember – you'll need it later, when you start the Akita Agent on the CLI.
Generate API key
On the same Settings page, locate and click the “API Keys” tab. Click the “Set up the Akita client” button. Copy your API key secret into your favorite password manager or somewhere else you can easily access it. Also note your API key, as you will need it later.
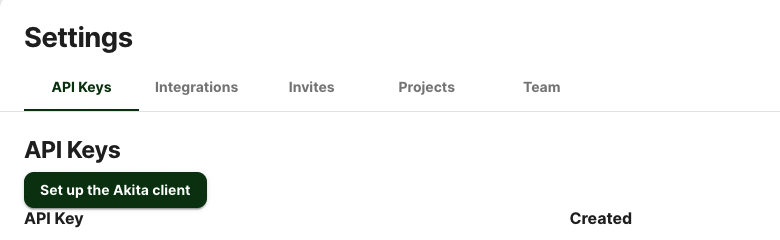
Install the Agent
To install the Akita Agent, run the following:
bash -c "$(curl -L https://releases.akita.software/scripts/install_akita.sh)"
Then log in using akita login.
Inject and Apply Deployment Template
-
Navigate to the directory that contains the Deployment YAML manifest(s) that you would like to inject the Akita agent into. This file should have at least one container that you would like to monitor with Akita
-
Run the following command to inject the Akita Agent as a sidecar container into your Deployments and apply them, replacing
<project_name>with the name of the Akita project that you want to send traffic data to and<deployment_file>with the name of your deployment YAML file:akita kube inject -s -p <project_name> -f <deployment_file> | kubectl apply -f -The
-sflag generates a Kubernetes Secret containing your Akita API key that the agent depends upon.As an example, to inject the Akita Agent into a deployment file called
mydeployment.yamland send traffic data to an Akita project calledmyproject, you would run the following command:akita kube inject -s -p myproject -f mydeployment.yaml | kubectl apply -f -
Write to a new file instead
Alternatively, if you would like to write the modified Deployment manifest to a new file instead of applying it directly to your Kubernetes cluster, you can use the --output (-o)flag. For example:
akita kube inject -s -p myproject -f mydeployment.yml -o injected.yml
You can then apply this file to your Kubernetes cluster using the kubectl apply command:
kubectl apply -f injected.yml
If you need more information on the kube inject command, see the kube inject and kube secret reference docs.
Verify
Find the pod that was created, and run the following command to see the Akita Agent output:
kubectl logs <pod name> akita
In the Akita web console, check out the incoming data on the Model page. You should see a map of your API being generated as the Akita Agent gathers data.
Then check out the Metrics and Errors page to get real-time information on the health of your app or service.
Adding an Akita Agent sidecar to a running Kubernetes pod
Below are instructions for starting a new ephemeral container with an Akita Agent sidecar in an existing Kubernetes pod.
Requirements
- Kubernetes v1.18+
- Alpha features in Kubernetes enabled
kubectly debugspecifically must be enabled
To get the Akita agent running as a sidecar in a new ephemeral container in a single Kubernetes service, you will:
- Meet the prerequisites
- Create an Akita Project
- Generate an API key for the Akita Agent
- Attach the Akita Agent as a sidecar
- Verify that the Akita Agent is working
Thanks to Bruno Felix, who experimented with this method and provided us with his examples!
Prerequisites
You’ll need to be in our beta.
Your Kubernetes service must:
- have access to the public internet
- use unencrypted HTTP
- be version 1.18 or higher
- have alpha features enabled
- have
kubectly debugenabled
Create a project
Log into the Akita App, and go to the Settings page.
Enter a project name and click "Create Project". We suggest naming the project after your app or deployment stack.
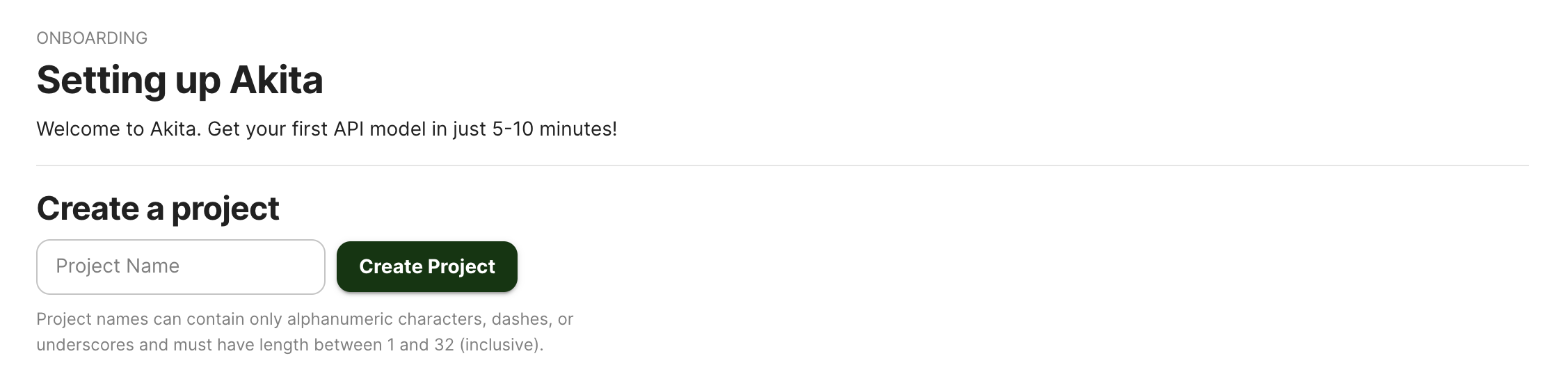
Give your project a name that's easy to remember – you'll need it later, when you start the Akita Agent on the CLI.
Generate API key
On the same Settings page, locate and click the “API Keys” tab. Click the “Set up the Akita client” button. Copy your API key secret into your favorite password manager or somewhere else you can easily access it. Also note your API key, as you will need it later.
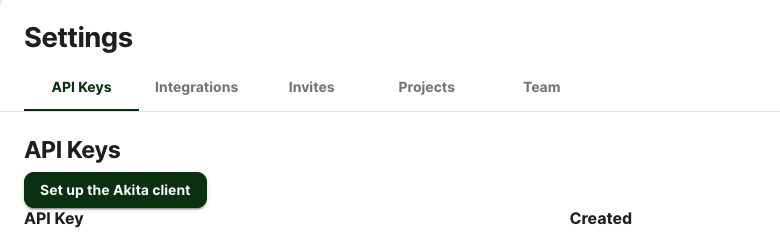
Attach Agent
To attach the Akita Agent as a sidecar:
- Identify the name of the pod that is running the app or service you want Akita to monitor.
- Identify the port the pod is running on.
- Run the below command, inserting your Akita Project name, API key ID, and key secret.
kubectl debug -it myservice-xyzabc \
--image=akitasoftware/cli:latest \
--env="AKITA_API_KEY_ID=$AKITA_API_KEY_ID" \
--env="AKITA_API_KEY_SECRET=$AKITA_API_KEY_SECRET" \
-- akita apidump --project my-project-name
Verify
If the command was successful, you will see the akita apidump output. Use Ctrl+C to stop the trace as if you were running normally from the command line.
In the Akita web console, check out the incoming data on the Model page. You should see a map of your API being generated as the Akita Agent gathers data.
Then check out the Metrics and Errors page to get real-time information on the health of your app or service.
Updated almost 3 years ago